
Suricata is the leading independent open source threat detection engine. By combining intrusion detection (IDS), intrusion prevention (IPS), network security monitoring (NSM) and PCAP processing, Suricata can quickly identify, stop, and assess the most sophisticated attacks.
One of the key advantage of Suricata is that it is multi-threaded, which means that it can use multiple cores at once, what allows Suricata to process multiple events at the same time without having to interrupt other requests. Multi-threading also enables Suricata to load balance across the CPUs, as well as improve overall performance in network traffic analysis.
Moreover Suricata is compatible with a range of thid party Snort tools and have very similiar rules syntax to Snort, what is convenient for engineers who want to switch to Suricata.
In this scenario we are combining Suricata with Energy Logserver SIEM.
Suricata operates on network stack and it is possible to deploy it as an agent on desired hosts or create a cluster, where copy of traffic would be sent via SPAN port. In this example we will use it as an agent.
This scenario starts with an example of an attack on web application server where Suricata agent is deployed. We will try to get a reverse shell to our attacking machine through a LFI vulnerability in a web app.
I set up my netcat listener on port 443 (non-TLS) and execute payload in a web app url:
http://192.168.184.130/DVWA/vulnerabilities/fi/?page=PAYLOAD
Payload deliberately is not shown in this example, cause this text are written to show capabilities of Suricata and not the hacking techniques.
As shown below, I got a connection from a web application server to my attacking machine:
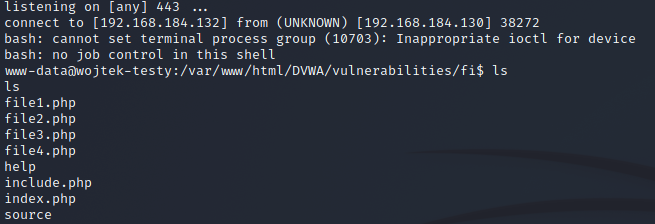
Suricata triggered 3 alarms at the beginning:
08/27/2021-13:29:28.466008 [**] [1:2022973:1] ET POLICY Possible Kali Linux hostname in DHCP Request Packet [**] [Classification: Potential Corporate Privacy Violation] [Priority: 1] {UDP} 192.168.184.132:68 -> 192.168.184.254:67
08/27/2021-13:40:50.067549 [**] [1:3174423:1] IDPS: base64 encoded PHP tags [**] [Classification: Web Application Attack] [Priority: 1] {TCP} 192.168.184.132:42980 -> 192.168.184.130:80
08/27/2021-13:41:03.932347 [**] [1:2271003:1] SURICATA non-TLS on TLS port [**] [Classification: (null)] [Priority: 3] {TCP} 192.168.184.130:37696 -> 192.168.184.132:443
- Detection of my Kali Linux machine in LAN in DHCP request packet,
- PHP payload encoded in base64,
- Traffic going to port 443 which supposed to be TLS, but is not.
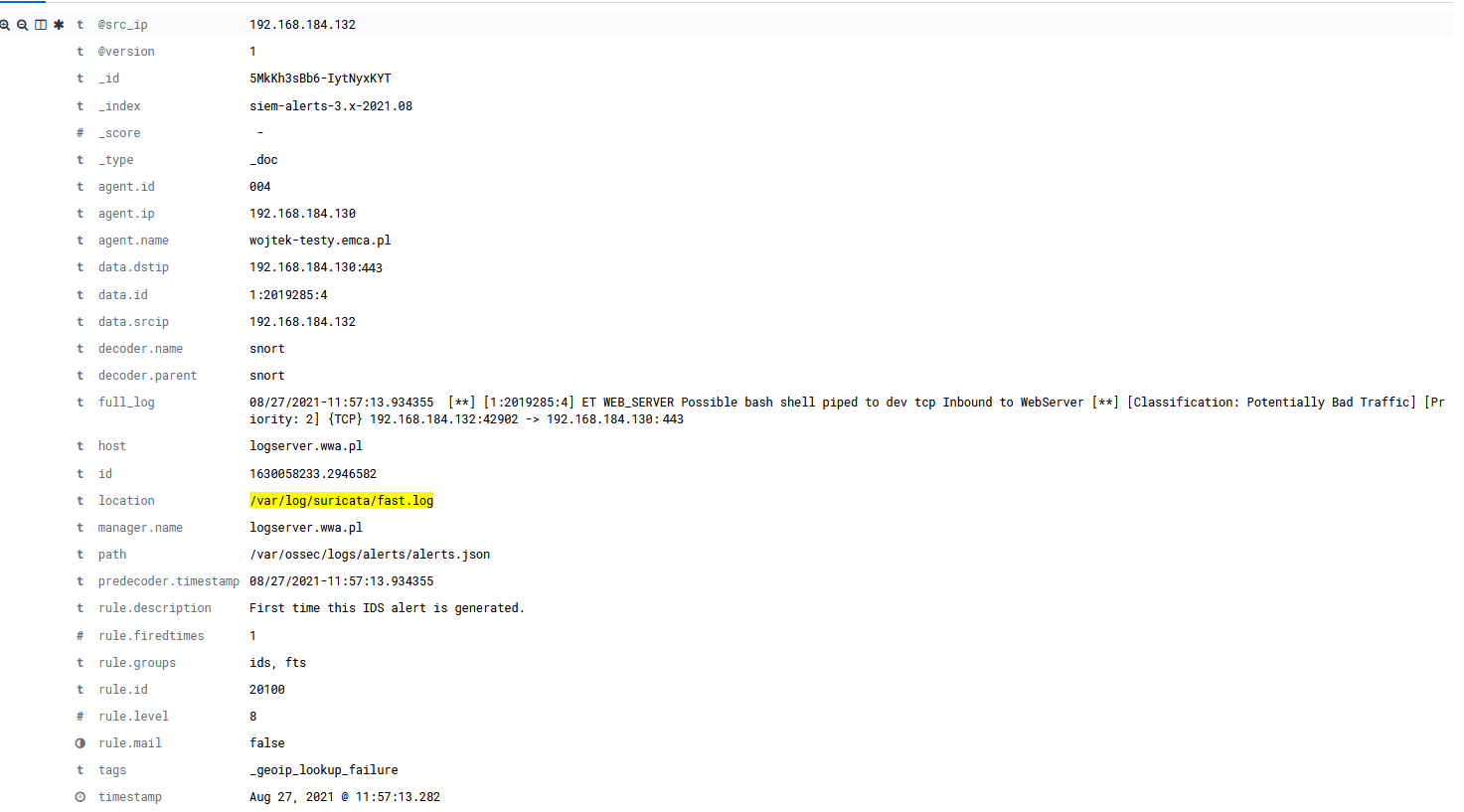
After all we can investigate final alarm – potential reverse shell connection – in Energy Logserver GUI:
Suricata has ability to block actions showed in the presented example through IPS module.
I will not discuss about IPS configuration, but we can set certain behavior while settings rulesets.
For instance:
Drop – if the program finds a signature that matches, containing drop, it stops immediately. The packet will not be sent any further. An alert will be generated.
Reject – send RST/ICMP unreach error to the sender of the matching packet. An alert will be generated.
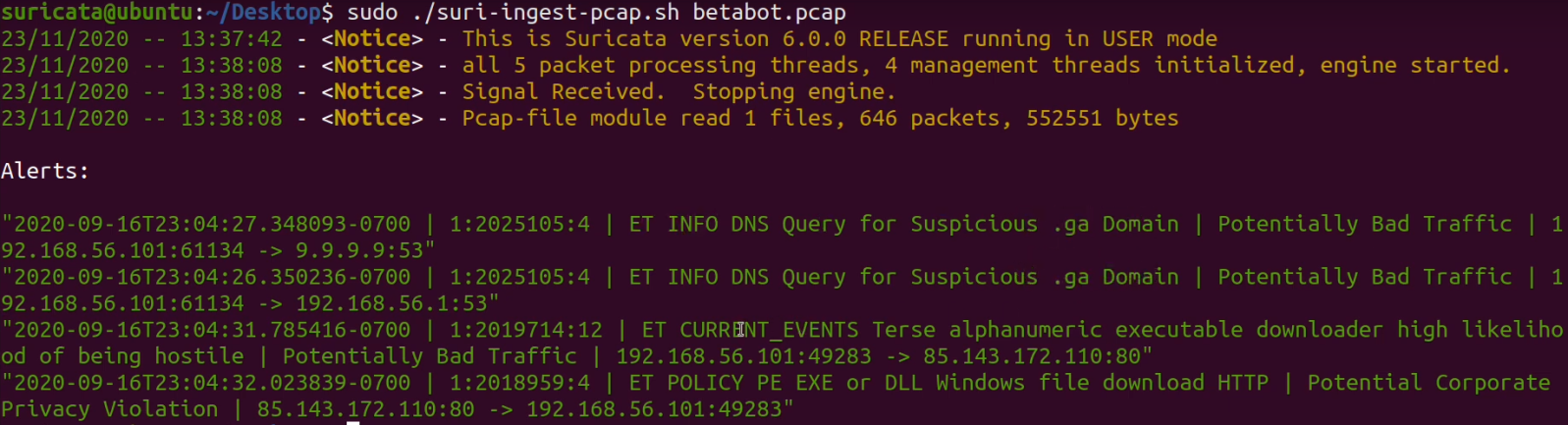
Suricata can be used also for malware analysis in pcap files.
In the example below I ingested pcap file to Suricata and triggered alarms typical for Betabot malware behavior:
Suricata can be used as an IDS or and IPS, where IDS is only able to detect malicious behavior and an IPS can both identify and handle malicious packets.
Suricata has also capability to investigate pcap files which can show anomalies detected in your corporate network traffic.

