
The Mitre Corporation is known for maintaining a knowledge base on attacks, spyware, exploits, and other cybersecurity threat areas. This knowledge has been classified and described as Mitre ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge). In practice, Mitre serves as a description of various techniques used by cybercriminals. These tactics are used by security analysts to understand what techniques may be employed by potential attackers.
The latest versions of ATT&CK include tactics such as:
- Initial Access
- Execution
- Persistence
- Privilege Escalation
- Defense Evasion
- Credential Access
- Discovery
- Lateral Movement
- Collection
- Exfiltration
- Impact
SIEM rules in Energy Logserver directly map encountered incidents to the Mitre ATT&CK matrix. Our solution provides a system equipped with hundreds of rules addressing 90 unique techniques.
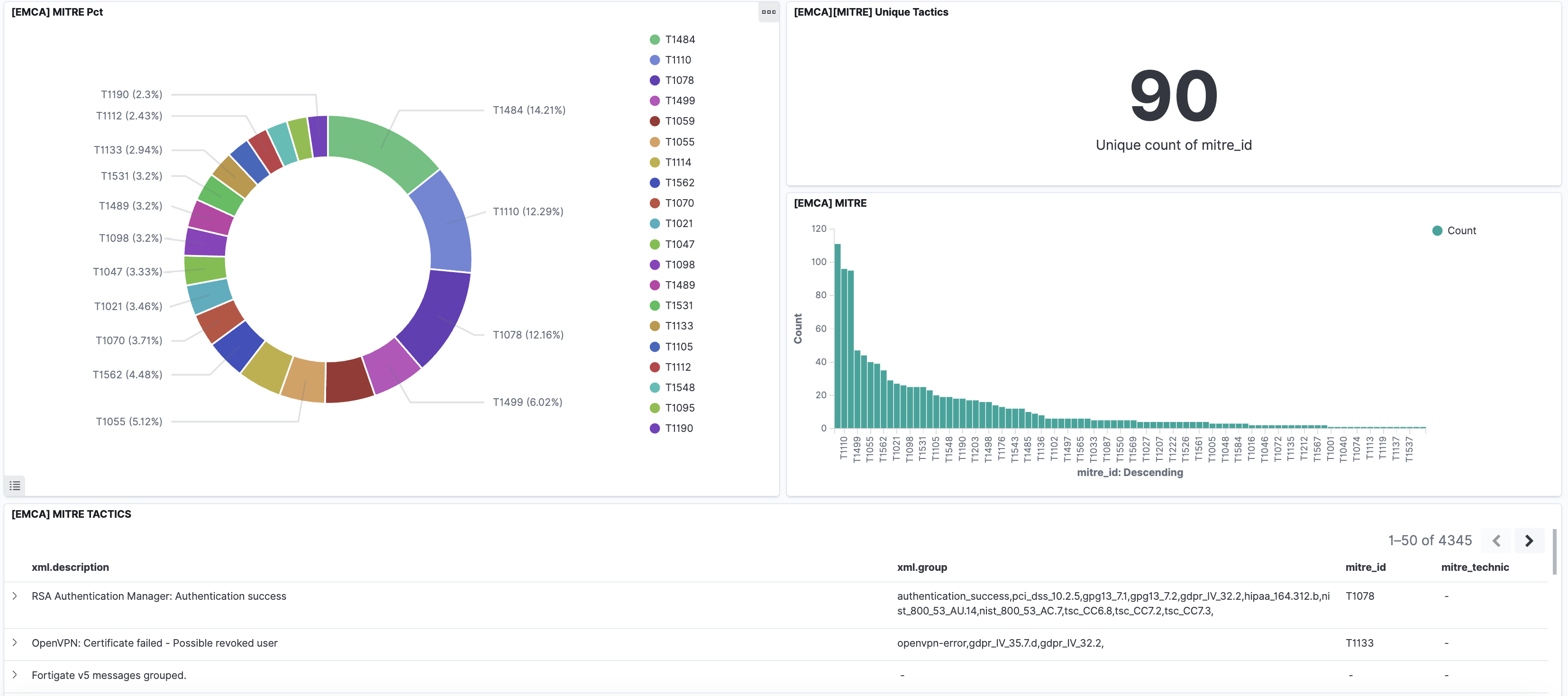
Mitre encompasses more than just log analysis, so SIEM cannot cover all areas of this classification. Additionally, the bars on the chart show that some techniques have greater coverage in rules than others.
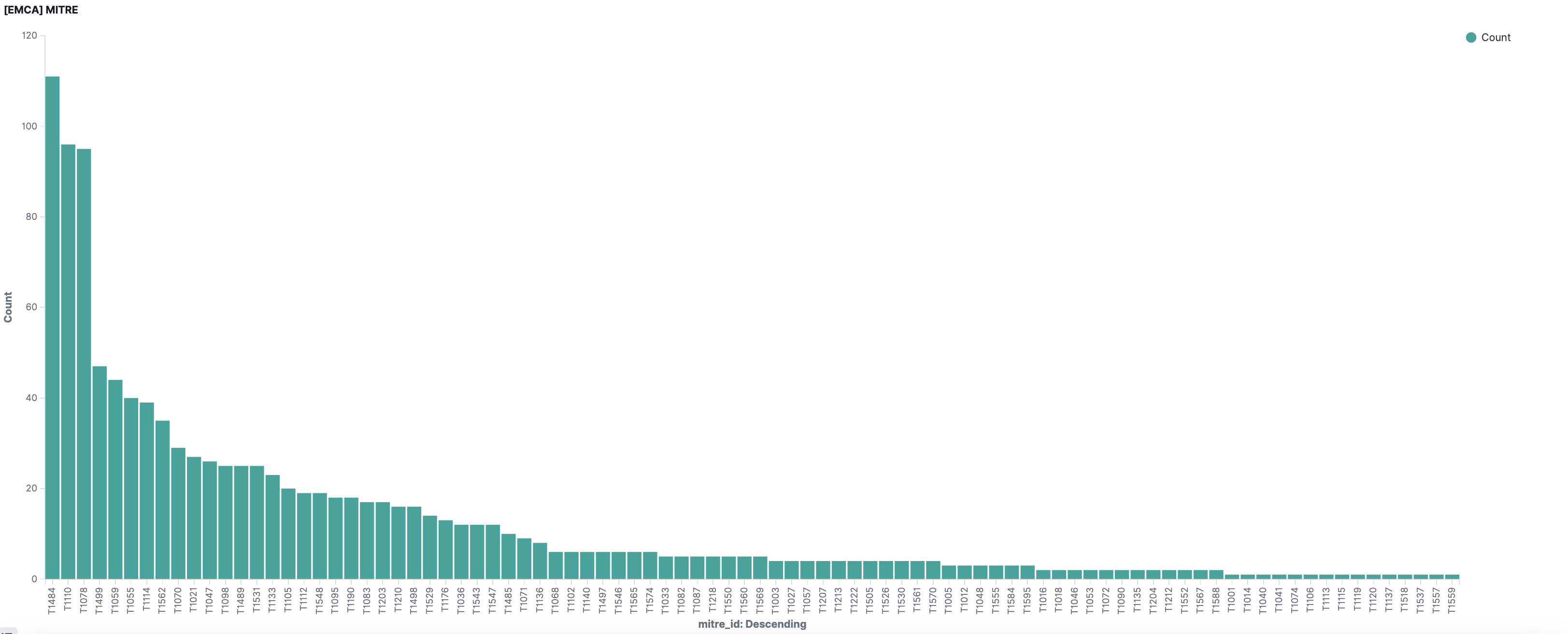
This event is also natural. Operations on user accounts and passwords are under special protection of SIEM detection rules.
Proper threat identification and rapid, conscious reaction are key elements in building an organization’s cybersecurity. A properly configured SIEM system, mapping the Mitre ATT&CK matrix, allows for effective counter against the growing number of threats.
It’s worth emphasizing that the tactics and attack techniques identified in Mitre ATT&CK are not secret knowledge reserved only for experienced SOC teams. Energy Logserver, equipped with correlation rules integrated with the Mitre matrix, is also an excellent tool in the hands of administrators and IT staff who are not specialized in cybersecurity on a daily basis.
In conclusion, integrating SIEM rules with the Mitre ATT&CK model in Energy Logserver provides a comprehensive approach to preventing and responding to cyber incidents. While SIEM cannot cover all areas of the Mitre classification, it effectively utilizes available rules to enhance protection against various attack techniques. By leveraging these tools, we can better understand and respond to evolving threats in cyberspace, ensuring a higher level of security for our data and infrastructure.
If you are interested in getting more information or implementing SIEM solution in your network, feel free to contact us.

